Have you ever wished you could go back in time...and un-do something you did? Windows' built-in recovery tool, System Restore allows your computer to do what you and I cannot do, jump back in history to a time when everything was working properly, and that's a pretty neat trick!
Tip of the day: I should caution you that System Restore is not a panacea-- there are some things it copies and restores and some things it doesn't.
* It does not recover data once the Recycle bin has been emptied -- you need to use Shadow Copy or an undelete utility for that.
* It doesn't recover lost or corrupted User passwords.
It is, however, "user friendly" and simple to use. It does, automatically, take "snapshots" of the Registry and some dynamic system files, and is a good way to get an unstable and/or non-booting system back on its feet again without losing your files and user settings.
To get started, you need to make sure that System Restore is turned on, and that it has at least 200 megabytes of free hard-drive space to store snapshots on.
Turn on System Restore by clicking Start and right-click My Computer >Properties >System Restore tab and make sure there's no check in the box next to "Turn off System Restore on all drives."
While you're there, select the drive, or partition, where you want to store the snapshots and click the Settings button. Now you can use the slider to denote the amount of memory you want to devote to System Restore. I set mine to about 500 MB's, which gives me a good selection of Restore Points (snapshots) without losing too much storage. And now you are set: Windows will start taking snapshots whenever you make a 'major' change, like installing a program or device driver.
There are a couple of different ways to use System Restore to go back in time. In the first scenario, Windows still functions, and boots, but is unstable and crashes or freezes frequently.
1) Use System Restore by clicking Start >Programs >Accessories >Sytem Tools >System Restore. This will launch the System Restore Wizard. By default, the radio button "Restore my computer to an earlier time" is already selected so hit the Next button.
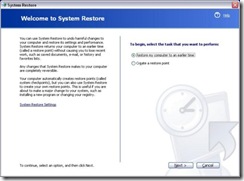
Now you will see a calendar, which has the available snapshots/times in bold.
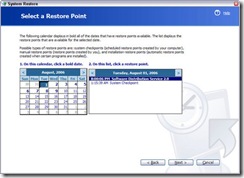
2) Start with the most recent one first, and click Next, and then OK. Your system will reboot, take a while to load, and then a message saying "Your system has been successfully restored to date selected" will appear.
If this doesn't happen, you will see an error message-- retry using the next most recent Restore Point. You may have to try several.
The next scenario is when you're in a bad situation where Windows just BSOD's ("blue screens"), or won't even boot. Boot your machine and hit, repeatedly, the F8 key as if you were trying to get into Safe Mode.
When the white-on-black Advanced Start Up screen appears do not hit any key(s) just yet. Before too long a dialogue will open asking whether you want to continue on into Safe Mode...Y/N? Type an "N" for "no". This will launch the System Restore Wizard and you follow the steps as outlined above.
Should this dialogue not open after a suitable wait, use your up/down arrow keys to highlight (select) "Safe Mode" and hit Enter. You will now be in the funny-looking, petite version of Windows called, you guessed it, "Safe Mode". It's easy to know that you are, because it clearly says Safe Mode in all four corners of your desktop. Now you can access System Restore through the Start >Programs menu. Again, follow the steps as outlined above.
Occasionally System Restore cannot undo all the damage and it doesn't work as we'd hoped. If the damage was done by malware such as a virus that also infected your snapshots, it may not work at all. But it is a powerful tool and has saved me many times over the years. It is quick, simple, and usually very effective-- and it's free!
[For more answers on System Restore, see my two follow-up posts; "A quick System Restore addenda", and "questions answered".]
Today's free link: I mentioned undelete utilities, and there are many out there for you to try. Try to recover files by starting with a scan using Softperfect File Recovery. "...a free and useful tool to restore accidentally deleted files from hard and floppy disks, USB flash drives, CF and SD cards and other storage media. It supports the popular file systems such as FAT12, FAT16, FAT32, NTFS and NTFS5 with compression and encryption. If your important files disappeared and you can’t find them in the recycle bin, try this software product and get the files back to life. Easy to use, no installation is required."
Copyright 2007-8 © Tech Paul. All rights reserved. post to jaanix
post to jaanix
![]() post to jaanix
post to jaanix