This story opens gently enough. It begins with a friendly and helpful Comment posted on a friendly and helpful blog.
Someone had written to share "the results of their work", which he said "solved his security problems." He was talking about viruses and spyware, and other malware, and he said his method "covers 99.8%! of all known threats."
He posted his advice/Comment on an article about How To prevent the dangers posed by spyware (and also warns about "rogue" anti-spyware programs). He signed himself "Spycrasher".
So far, this all sounds pretty good, doesn't it? 99.8% effective certainly sounds good.
As you have probably deduced, Dear Reader, the "friendly and helpful blog" in question was this one. Tech--for Everyone, like most blogs, provides readers the opportunity to respond, ask a question, or just "put in their two cents", simply by clicking on "Comments" at the bottom of the article. And also like most blogs, I have the ability to "moderate" which comments get posted and which don't-- for instance, Comments containing offensive language will not be published.
Spycrasher's 99.8%- effective security solution will NOT be seen here.
But.. maybe you're a little curious as to what it was. And.. maybe, why I deleted it. (Take another peek at today's title..) "Spycrasher's" comment said to use three particular anti-spyware programs-- in tandem-- and he provided download links. (This, alone, triggers red flags.) He mentioned two tools I was not familiar with, and one rather well-known program.
* Hyperlinks are always suspicious (and blocked as a matter of policy), and the first thing I checked was, did the links point to legitimate websites..? Or would clicking on them take you to a poisoned webpage (which could infect your machine) or a pharming site.
No problem there. The links he provided did indeed point to real websites.
* The next thing was to check out the unknown programs themselves. No self-respecting and legitimate tech writer will advocate something they have not used, and tested, themselves. Period.
In my initial research of the first program (XoftSpy-SE), I found a wide range of reviews and comments.. from "this is rogue" to "this is the best thing since sliced bread", and I learned that the program was "for pay".
I don't promote "for pay" software here (but do provide a daily free download), nor, even potentially rogue app's; and so I stopped right there. I would not allow Spycrasher's Comment.
* Being the gentleman that I am, I decided to write Spycrasher and thank him for his submission, and explain why I had moderated it. But before I did, I wanted to get a feel for where he was coming from.. so I ran a Whois on his IP...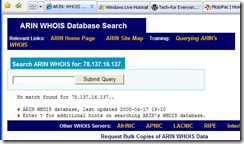
Now, I gotta tell you.. it is very rare for ARIN to come back with a "no match found". Very, very strange.
So I traced him.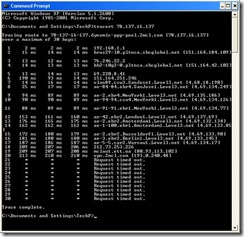
New York >London >Amsterdam >Berlin >Warsaw...
And then he disappears into a virtual private network somewhere in the Ukraine.
Odd.
* So I used a search engine to find instances of the word "Spycrasher"... and he came up a lot. Spycrasher likes to post in various forums. Quite a few of them, actually. Like, practically all of them.
And he posts a lot of Comments there.
* Guess what? They are all identical to the the one he posted (I should say "pasted") on mine.. right down to the 'wink' smiley ;-).
Very.. odd.
Tip of the day: Be very leery of hyperlinks, folks.. and please understand: not every innocent looking thing you see on the Internet is in fact "friendly and helpful". There are people whose full-time job it is to try to trick you, and seduce you into doing something you normally wouldn't.
I am very sad to say.
[note to bloggers/forum moderators/webmasters: you may want to search your published pages for instances of "Spycrasher", and delete this guy.]
Today's free link: I am going to repost a program here today, because I have it on every single one of my (Windows) machines, and I think you should too. ThreatFire (originally named "CyberHawk") is a free, behavior-based anti-malware application. I use it as a supplement to my antivirus and other anti-spyware tools. Heuristic tools like ThreatFire are your only defense against "zero day" exploits.
Copyright 2007-8 © Tech Paul. All rights reserved*.![]() post to jaanix
post to jaanix
| Share this post : |


No comments:
Post a Comment