If you turn on your computer and Windows fails to load to your Desktop, but instead displays the following error message, Unexpected Interrupt In Protected Mode, there are a couple of things that might be happening. Here are some troubleshooting steps which you can try to get your machine up and running again.
First, try rebooting your machine. If that doesn't "cure" it, keep reading.
Causes: causes for this particular error message may be hardware-related: a failed or failing motherboard, or failing (or over-heating) CPU, or it may be related to a corrupted BIOS. Since the hardware issues most likely will require replacement parts and/or a trip to the shop, lets first tackle the BIOS possibility.
What is a “BIOS”? Your computer’s BIOS is a very basic set of instructions that tells your machine where to look for a keyboard and mouse and an operating system. It runs when your machine is first powered on. To make changes in the BIOS, you’re going to interrupt the boot process before Windows loads, so you need to use a keyboard that is plugged into the PS/2 port on the back of the machine, and not a wireless one.
1) Reboot your machine, and get ready to act quickly. Very early you will see a little bit of text that says, “hit F2* to enter setup.” (*Different manufacturers use different keys-- F2 is the most common, but it may be the Esc key, Del, or F10. Refer to your computer builder's website if you cannot determine which key to press.) Rapidly hit the suggested key several times, and enter “Setup” — this is your BIOS control panel. 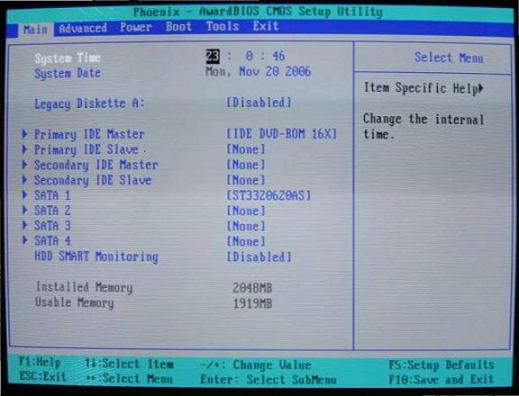
2) Look to the bottom of the screen for Setup's menu choices. Now look for the Function Key choice that will reset the BIOS to its default configuration. This is frequently the F5 key, but it may be F6.. In the screenshot above, look to the lower right: for this BIOS, it is F5 we want. "Setup Defaults".
3) Save and Exit the Setup utility, and reboot. (In the sample BIOS, that's the F10 key. But you may have to hit Esc, an then answer "Yes" to the Save? question. It varies.)
If resetting the BIOS to its defaults does not restore Windows functionality, I recommend you take your machine in to a qualified tech who can determine the hardware issues.
If it did restore it, you want to ask yourself what caused the BIOS corruption? Usually the answer is a recently installed program, or malware-- be sure to run an antivirus scan.
Today's free link: DriverScanner from Uniblue. Scan, backup, and Update your PC's drivers. Folks-- I have not yet used this new tool, but I learned of it from Bill Mullins, who is as reliable a source as I have ever run across. To read his review, click here.
Copyright 2007-8 © Tech Paul. All rights reserved.![]() post to jaanix
post to jaanix