“System Restore won’t work”, “I’m worried about ID Theft, how do I know if an email is legit?”, “I can’t get this #$*& program out of my Startup folder” — these are examples of some of the questions I have received since posting my articles on these 
Tip of the day: Since I’m going to cover the questions above, there is not going to be a single “Tip of the day” today. Instead, there will be “Today’s three questions”…
More on System Restore: What to do when System Restore just refuses to work. As I mentioned in my first System Restore post, SR simply is not a failsafe miracle worker. There are troubles that can occur that it simply does not repair — such as a corrupted SAM database. It is however a good place to start. It does undo a lot of the damage you can accidentally do to your machine. This fact is why you should always make a back up of your system — either a “disk image” made with a 3rd-party utility like Acronis True Image, or Norton Ghost, and/or Windows Backup Utility (Start >Programs >Accessories >System tools >Backup).
** My illustrated tutorial for that is here.**
I stated in the prior article, and will repeat here, that you may have to repeat the System Restore process several times before one “snapshot” finally takes. When you use SR, you will see a calendar with available snapshots in bold dates. You should see several. Start with the most recent date and time, and work your way backwards. If you have done this with no luck, you probably have one of those troubles System Restore is not designed for. Either look elsewhere for solutions, or call for some Tech Support (we Tech Support folks need to make a living too, you know).
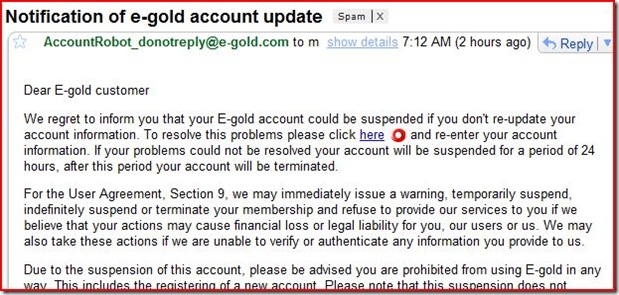
Legit vs. Phishing: “how do I know if an email is legit?” In my post about the rocket scientist, I discussed phishing and recommended an anti-phishing site toolbar, which combats a form of phishing called “pharming“.
I suggest you take no chances with emails.
* Simply do not click on links in emails.
* Also, realize that your bank will not send you links. They know about phishing, and they figure you already know their url (you should have it bookmarked, so use that…or call them directly).
* Also be aware that just because an email claims to be from a friend or relative, doesn’t mean that it is. If you are not expecting an “executable” (application) or “you gotta see this!” .jpeg from Uncle Fred, by all means don’t open it! Contact him and ask him, “did you send me a..?” It is an easy thing for an Evil Doer to 'spoof' an address.
* And finally, make sure your antivirus definitions are up to date. If it is not already on by default, open your antivirus’ Options and look in “Update Options” for “Download and install new definitions automatically” (or words to that effect) and make sure it’s selected. If available, have it set to scan email and email attachments as well. (And, if your AV cannot scan incoming e-mail.. think about switching to one that does!)
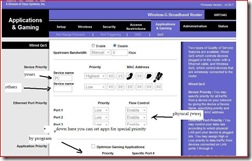
Removing stubborn start up programs: If the methods I described in “My Startup folder is a clown car” proved insufficient for getting rid of a really determined program, there are more methods you can try. The first is using the msconfig tool.
Start by opening the msconfig utility. Click Start >Run and type in “msconfig” (no quotes), and then click on the Startup tab. Here you will see a list of the programs scheduled to start when Windows boots. Uncheck the checkbox next to the program you are having the troubles with. You will need to restart your system for the changes to take effect.
**Vista users: Manage Startup programs in Vista**
If you have already tried the aforementioned methods and simply cannot kill the autolaunch, please consider simply using Add/Remove Programs to “retire” the troublesome program altogether…or install a startup manager program like StartUp Cop.
Today’s free link: GIMP Open Source digital image manipulating tool. This completely free application is a bit tricky to install but is well worth it as it offers a full range of tools for adjusting your digital images, and it does that in an interface that’s comfortable to folks with Photoshop experience.
Copyright 2007-8 © Tech Paul. All rights reserved.